Insight
Tackling the Challenge of Employing Industrial Cybersecurity to Protect Public Water Systems (PWSs)
Taking Steps to Safeguard Facilities
Three Things You Can Do to Get Started
- Use the EPA memorandum to secure funding. Implementing a cybersecurity program costs money. Many PWSs do not have the resources to go it alone, so gaining access to government support is the first step on the road to meeting the new requirements.
- Leverage the memorandum to get management buy-in. Developing and implementing a successful cybersecurity program requires top-down support. The EPA memorandum lines out the objectives each PWS has to meet and serves as a platform for building the executive leadership involvement that is vital to success.
- Take advantage of existing knowledge. Other industries across the country have implemented workable cybersecurity plans and some PWSs already have established cybersecurity programs, so there is no need to reinvent the wheel. Seek out experts and capitalize on “lessons learned” to put your cybersecurity program together.
SWOT24™, Operational Technology (OT) Cybersecurity by ABS Group, is helping PWSs protect their drinking and wastewater plant operations from cyber attacks with a consequence-driven methodology that considers the following risk variables:
- Threat – an occurrence or action that has the potential to harm life, information, operations, the environment and/or property
- Vulnerability – physical feature or operational attribute that exposes a PWS to exploitation or a given hazard
- Consequence – effect of an event or incident.
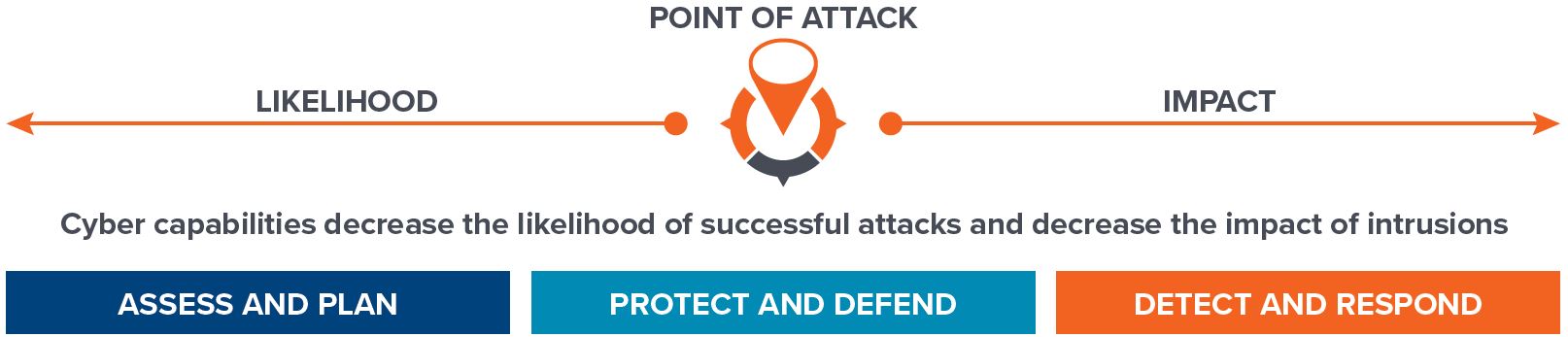
By using this methodology, cyber threats are prioritized by criticality and represented visually in a bowtie model that shows the steps taken to minimize the likelihood of a cyberattack and mitigate the consequences if cybersecurity is breached.
The SWOT24 team of experts works with clients in multiple industries to understand the cyber risks that are unique to the digital and computer-based systems that run industrial operations, also known as Operational Technology (OT) and help build security solutions that are relevant to OT systems, effectively and manageably.
Additionally, SWOT24 can help operationalize your OT cybersecurity program with our Industrial Security Operations Center (ISOC), staffed with OT cybersecurity experts that help you identify, respond to, remediate and recover from cyber attacks with 24/7/365 system monitoring.
Why SWOT24?
We're the Experts
SWOT24™, OT Cybersecurity by ABS Group, provides a comprehensive portfolio of OT cybersecurity consulting, implementation and risk management services. We help organizations, like yours, identify and mitigate critical cyber threats in real-time. We focus on stopping the bad guys so you can focus on what really matters: Your Operations.
