Insight
Infographic: Managing the Risks of Integrating IT and OT Systems
ABS Group Applied Technology and Data Analytics Services
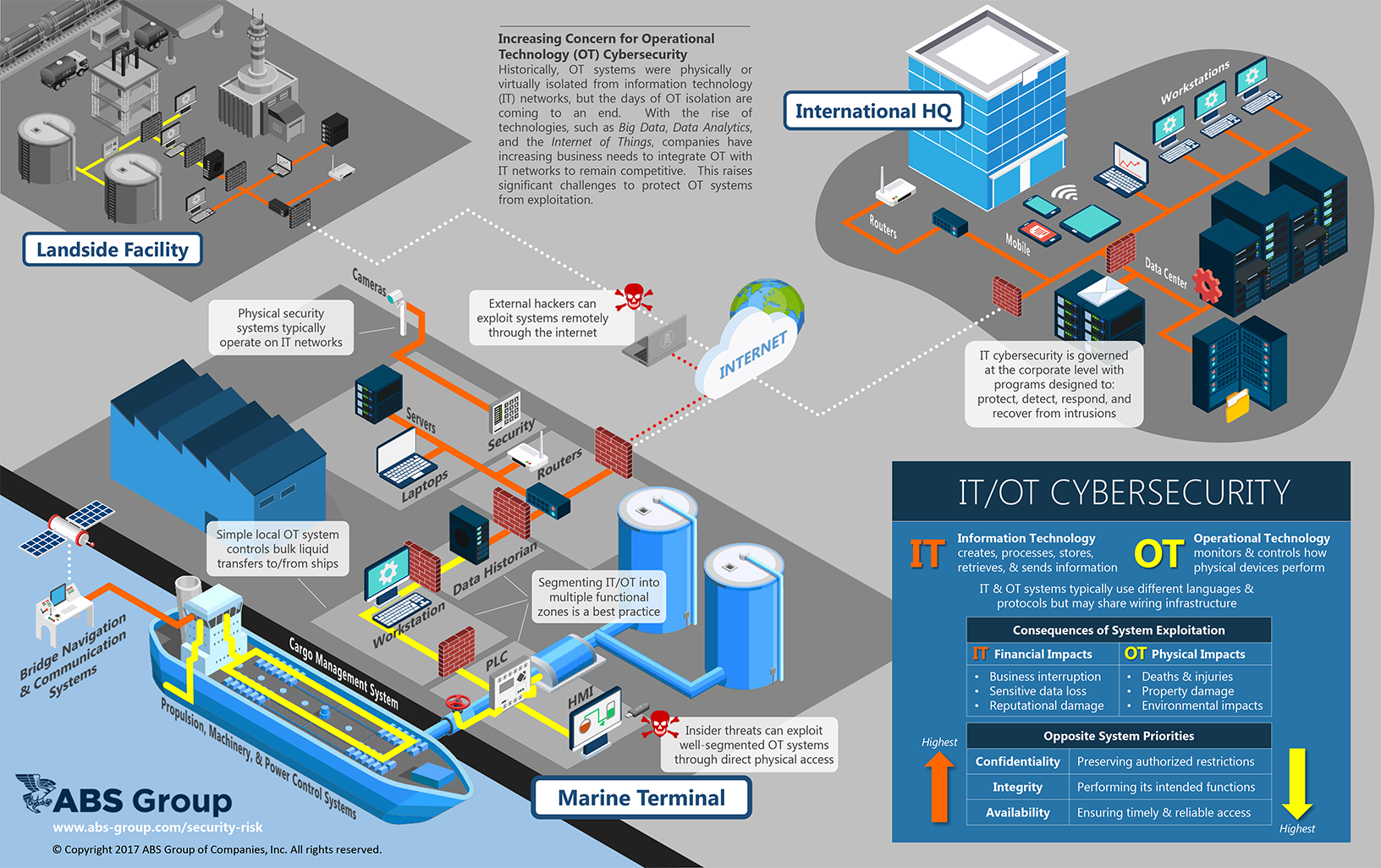
Today, companies are very concerned with cybersecurity; however, their focus is generally on protecting IT networks from the theft of proprietary or personal data. Cybersecurity is typically governed by the corporate IT departments focusing on protecting data and ensuring the availability of critical business systems by implementing a robust cybersecurity program that includes:
- Executive-level oversight by a chief information security officer (CISO)
- Governing policies and procedures
- Cybersecurity training
- Detailed vulnerability assessments performed against a range of proprietary and international standards
- Cyber-related incident response plans
While IT cybersecurity is mature, relatively few companies extend their cybersecurity programs to address OT systems. Many companies have inadequate OT cybersecurity and lack the controls that are commonplace in IT networks, such as configuration management, contingency plans, access control policy and authentication policy. OT system managers are primarily concerned with the availability and reliability of the system and less so with the security because, historically, OT systems have been isolated from IT networks. However, due to increasing business demands, the days of OT isolation are coming to an end.
As companies weigh the pros and cons of IT/OT integration, many see this integration as inevitable. So, to ensure that new vulnerabilities are not introduced as these systems are integrated, companies must carefully design their cybersecurity architecture and establish robust protections.